Understanding VLANs: Tagged, Untagged, and Native VLANs

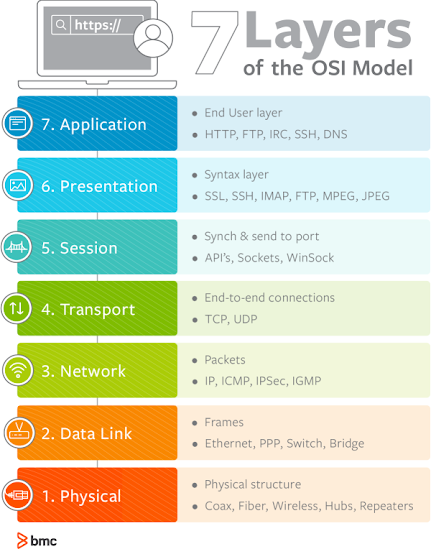
What is VLAN ?? Virtual Local Area Networks (VLANs) are a fundamental concept in modern networking, allowing us to segment a physical network into multiple logical networks. By creating VLANs, we can isolate traffic, enhance security, and improve network performance. However, to fully utilize VLANs, it's crucial to understand the differences between tagged, untagged, and native VLANs. Untagged VLANs Untagged VLANs are the default configuration for most network devices. When a device sends a packet to a switch, it does not include any VLAN information. The switch then assigns the packet to a specific VLAN based on the port configuration. For example, if a port is configured as an untagged member of VLAN 10, any untagged packets received on that port will be associated with VLAN 10 . Untagged VLANs are typically used for end devices that do not support VLAN tagging, such as workstations, IP cameras, and some servers. These devices simply want to communicate on the netw...