What is OSI Model | How OSI Model works ?
INTRO TO OSI Model
[ Open Systems Interconnection ]
In the early 1980s, the development of networks was chaotic. Each vendor had its own proprietary solution(PC). The bad part was that one vendor’s solution(PC) was not compatible with another vendor’s solution (PC) ex. IBM and Microsoft both are developing they own standard so only Microsoft can communicate with Microsoft computer and IBM can communicate with IBM computer. This is where International Organization for Standardization (ISO) come in action and ISO developed an Open model called OSI Model ( Open System Interconnection ),OSI comes with a Layering approach to the network or hardware vendors would design hardware for network, and others could develop software for the application for this hardware or network. Using an open model which everyone agrees so means we can build a network that is compatible with each other.
The OSI Model is a conceptual Model, Nowadays most vendors build networks based on the OSI model, TCP/IP, and hardware from different vendors is compatible with each other.
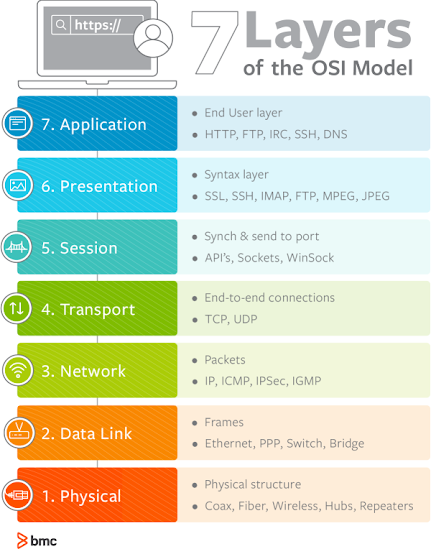
Here’s What the OSI model Looks like:
Technique to remember the 7 layers of the OSI:
“People Do Need To See Pamela Anderson”
Seven layers of OSI Model?
7. Application layer:
This is the only layer that directly interacts with data from the user. Software applications like web browsers and email clients rely on the application layer to initiate communications. But it should be made clear that client software applications are not part of the application layer; rather the application layer is responsible for the protocols and data manipulation that the software relies on to present meaningful data to the user. Application layer protocols include HTTP as well as SMTP (Simple Mail Transfer Protocol is one of the protocols that enables email communications).
6 Presentation layer:
This layer is primarily responsible for preparing data so that it can be used by the application layer; in other words, layer 6 makes the data resentable For the application layer so it can use. (like HTTP) The presentation layer is responsible for the translation, encryption, and compression of data.
Two communicating devices may be using different encoding methods, so layer 6 is responsible for translating incoming data into a Syntax that the application layer of the receiving device can understand.
If the devices are communicating over an encrypted connection, layer 6 is responsible for adding the encryption on the sender’s and as well as decoding The encryption on the receiver’s end so that it can present the application layer with unencrypted, readable data.
5.Session layer:
This is the Layer responsible for opening and closing communication between the two devices. The time between when the communication is opened And closed is known as the session. The session layer ensures that the session stays open long enough to transfer all the data being exchanged, and then Promptly closes the session in order to avoid wasting resources.
The session layer also use checkpoints (for Example: if 10MB file is being transferred, the session layer set a checkpoint after every 2MB. If connection crash after 5MB have been transferred, the session could be resumed from the last checkpoint, meaning only 5MB more MB of data need to be transferred ) Without checkpoint the entire transfer data would have to begin again from 0MB.
4. Transport Layer:
The basic function of the Transport layer is to accept data from the layer above, split it up into smaller units, pass these data units to the Network layer, and ensure that all the pieces arrive correctly at the other end.
Furthermore, all this must be done efficiently and in a way that isolates the upper layers from the inevitable changes in the hardware technology.
The Transport layer also determines what type of service to provide to the Session layer, and, ultimately, to the users of the network. The most popular type of transport connection is an error-free point-to-point channel that delivers messages or bytes in the order in which they were sent.
The Transport layer is a true end-to-end layer, all the way from the source to the destination. In other words, a program on the source machine carries on a conversation with a similar program on the destination machine, using the message headers and control messages.
Functions of Transport Layer
1.Service Point Addressing: Transport Layer header includes service point address which is port address. This layer gets the message to the correct process on the computer unlike Network Layer, which gets each packet to the correct computer.
2.Segmentation and Reassembling: A message is divided into segments; each segment contains sequence number, which enables this layer in reassembling the message. Message is reassembled correctly upon arrival at the destination and replaces packets which were lost in transmission.
3.Connection Control: It includes 2 types:
* Connectionless Transport Layer : Each segment is considered as an independent packet and delivered to the transport layer at the destination machine.
* Connection Oriented Transport Layer : Before delivering packets, connection is made with transport layer at the destination machine.
4.Flow Control: In this layer, flow control is performed end to end.
5.Error Control: Error Control is performed end to end in this layer to ensure that the complete message arrives at the receiving transport layer without any error. Error Correction is done through retransmission.
3. Network Layer:
The network Layer controls the operation of the subnet. The main aim of this layer is to deliver packets from source to destination across multiple links (networks). If two computers (system) are connected on the same link, then there is no need for a network layer. It routes the signal through different channels to the other end and acts as a network controller.
It also divides the outgoing messages into packets and to assemble incoming packets into messages for higher levels.
In broadcast networks, the routing problem is simple, so the network layer is often thin or even non-existent.
Functions of Network Layer
1.It translates logical network address into physical address. Concerned with circuit, message or packet switching.
2.Routers and gateways operate in the network layer. Mechanism is provided by Network Layer for routing the packets to final destination.
3.Connection services are provided including network layer flow control, network layer error control and packet sequence control.
4.Breaks larger packets into small packets.
2. Data Link Layer:
Data link layer performs the most reliable node to node delivery of data. It forms frames from the packets that are received from network layer and gives it to physical layer. It also synchronizes the information which is to be transmitted over the data. Error controlling is easily done. The encoded data are then passed to physical.
Error detection bits are used by the data link layer. It also corrects the errors. Outgoing messages are assembled into frames. Then the system waits for the acknowledgements to be received after the transmission. It is reliable to send message.
The main task of the data link layer is to transform a raw transmission facility into a line that appears free of undetected transmission errors to the network layer. It accomplishes this task by having the sender break up the input data into data frames(typically a few hundred or few thousand bytes) and transmit the frames sequentially. If the service is reliable, the receiver confirms correct receipt of each frame by send back an acknowledgement frame.
Functions of Data Link Layer
1.Framing: Frames are the streams of bits received from the network layer into manageable data units. This division of stream of bits is done by Data Link Layer.
2.Physical Addressing: The Data Link layer adds a header to the frame in order to define physical address of the sender or receiver of the frame, if the frames are to be distributed to different systems on the network.
3.Flow Control: A flow control mechanism to avoid a fast transmitter from running a slow receiver by buffering the extra bit is provided by flow control. This prevents traffic jam at the receiver side.
4.Error Control: Error control is achieved by adding a trailer at the end of the frame. Duplication of frames are also prevented by using this mechanism. Data Link Layers adds mechanism to prevent duplication of frames.
5.Access Control: Protocols of this layer determine which of the devices has control over the link at any given time, when two or more devices are connected to the same link.
1. Physical Layer
Physical layer is the lowest layer of the OSI reference model. It is responsible for sending bits from one computer to another. This layer is not concerned with the meaning of the bits and deals with the setup of physical connection to the network and with transmission and reception of signals.
Functions of Physical Layer
Following are the various functions performed by the Physical layer of the OSI model.
1.Representation of Bits: Data in this layer consists of stream of bits. The bits must be encoded into signals for transmission. It defines the type of encoding i.e. how 0's and 1's are changed to signal.
2.Data Rate: This layer defines the rate of transmission which is the number of bits per second.
3.Synchronization: It deals with the synchronization of the transmitter and receiver. The sender and receiver are synchronized at bit level.
4.Interface: The physical layer defines the transmission interface between devices and transmission medium.
5.Line Configuration: This layer connects devices with the medium: Point to Point configuration and Multipoint configuration.
6.Topologies: Devices must be connected using the following topologies: Mesh, Star, Ring and Bus.
7.Transmission Modes: Physical Layer defines the direction of transmission between two devices: Simplex, Half Duplex, Full Duplex.
8.Deals with baseband and broadband transmission.











nice work it helped a lot really
ReplyDeleteGreat post, you have pointed out some excellent points, I as well believe this is a very superb website.External Network Penetration Testing
ReplyDeleteReally Nice post, I got useful learning from here, keep sharing such a wonderful information with us, really inspired by your blog.
ReplyDeletelatest tech news
Great list! You can also add our Lifestyle & beauty blog too. It has 28 DA ;-).
ReplyDeleteDigital Era