What is OSI Model | How OSI Model works ?
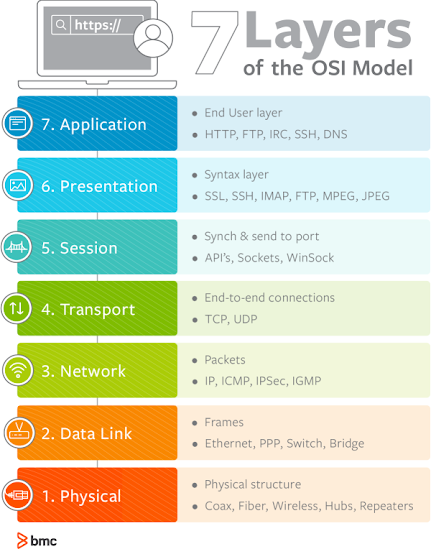
INTRO TO OSI Model [ Open Systems Interconnection ] In the early 1980s , the development of networks was chaotic. Each vendor had its own proprietary solution(PC). The bad part was that one vendor’s solution(PC) was not compatible with another vendor’s solution (PC) ex. IBM and Microsoft both are developing they own standard so only Microsoft can communicate with Microsoft computer and IBM can communicate with IBM computer. This is where I nternational Organization for Standardization (ISO) come in action and ISO developed an Open model called OSI Model ( Open System Interconnection ) ,OSI comes with a Layering approach to the network or hardware vendors would design hardware for network, and others could develop software for the application for this hardware or network. Using an open model which everyone agrees so means we can build a network that is compatible with each other. The OSI Model is a conceptual Model...